The New Kid on the Block
Digital assets have started moving from the sideline to the center of business finance. Companies can now park Bitcoin on their balance sheet or use stablecoins to settle bills in minutes, but this speed and flexibility is only one side of the coin. A lost private key or a compromised exchange can wipe out funds instantly, and fast-changing regulations can saddle a company with unexpected liability. Solid custody planning is no longer optional. We’ll take a look at today’s regulations and how they affect different kinds of organizations. Next, we’ll weigh three ways to secure digital assets: self custody, institutional custody, or collaborative custody, laying out the pros and cons for each approach. After that, our focus will shift toward safe self-custody: multi-sig wallet setups, key distribution, and internal policies. A short decision tree at the end will help match these options to your risk profile and day-to-day needs.
Custody Options
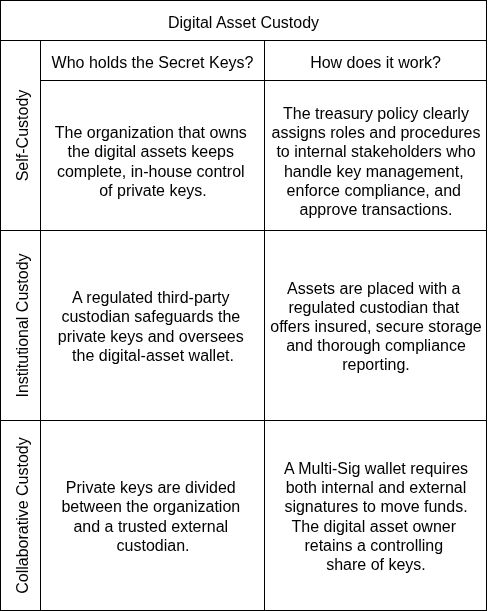
In general, there are three ways an organization can manage digital asset reserves and the secret keys associated with a digital asset wallet.
Regulatory Considerations
Organizations managing digital assets must navigate regulations that vary depending on their legal structure, jurisdiction, and whether they hold client funds or only their own reserves.
Investment funds:
In the U.S., investment funds must entrust client assets to a “qualified custodian”: a financial institution that satisfies the regulatory standards set by the SEC and FINRA under the Investment Advisers Act of 1940’s Custody Rule (Rule 206(4)–2). In other words, investment funds have two options: use a qualified custodian for client assets or become a chartered qualified custodian.
Must use a Qualified Custodian (regulated by SEC and FINRA). Alternative: become a chartered Qualified Custodian (requires licensing and compliance overhead).
Corporations (Holding Client Assets):
In the U.S., any corporate entity that transmits or holds digital assets on behalf of others falls under the definition of a Money Services Business. As a result, organizations must comply with specific regulations set forth by FinCEN under the Bank Secrecy Act. Any business accepting and transmitting convertible virtual currency owned by a third party must register as an MSB within 180 days of commencing operations (per the Money Laundering Suppression Act of 1994 31 CFR § 1022.380). To meet these standards, a business must create and implement their own AML (Anti-Money Laundering) program that conducts customer due diligence and reports suspicious activity under the BSA.
Classified as Money Services Businesses (MSBs) under FinCEN rules. Must register with FinCEN within 180 days of starting operations. Required to implement AML programs for customer due diligence and suspicious activity reporting under the Bank Secrecy Act (BSA).
Corporations (Holding Only Own Assets):
Corporations that do not hold client assets face fewer regulatory requirements. In fact there are no laws that specifically state how a non-bank corporation must self-custody its own digital assets. Industry specific regulations may apply if your corporation is itself regulated, but internal policies for custody are usually set by industry best-practice frameworks like NIST SP 800-53 or ISO 27001. While neither of these standards explicitly cover digital asset custody, they provide guidance on security management and access controls. With that being said, there are rules when it comes to reporting digital assets. Under GAAP, digital assets must be recorded at fair value and evidence of existence is required. If a public company holds cryptocurrency, Sarbanes-Oxley demands SOX controls for accounting accuracy over financial reporting under the Sarbanes-Oxley Act of 2002.
Not regulated as MSBs; fewer direct rules. No specific U.S. laws detailing self-custody requirements.Industry best practices recommended (NIST SP 800-53, ISO 27001). Reporting obligations under GAAP (record assets at fair value, demonstrate existence). For publicly traded companies, Sarbanes-Oxley compliance is required (internal controls over financial reporting accuracy).
Although non-bank corporations face less regulatory scrutiny than their MSB counterparts, it’s vital that any organization managing digital assets adhere to existing best practices. The industry is still nascent, and regulators may be unforgiving when setting precedents for regulation. Above all, best practices and robust controls are the best safeguards against costly mistakes and litigation.
Institutional Custody
Institutional Custody Benefits
Organizations prioritizing security, compliance, and asset safety usually elect to use a qualified custodian for storing their digital assets. Qualified custodians are held to higher regulatory standards, including mandatory asset segregation, third party audits and quarterly statements for clients. Trusted Anchorage Digital, Coinbase Custody, Fidelity and Gemini all offer custody services and are classified as qualified custodians.
Services offered by qualified custodians:
- Hot and Cold wallets: Most qualified custodians can offer both Hot and Cold wallets
- Multi–Signature wallets
- Insurance coverage
- Secured physical vaults
Organizations that need quick access to liquid markets often keep a portion of their assets on exchanges. When operating in the U.S., it is essential to use a registered Money Services Business (MSB) that complies with regulatory standards set by the SEC and FinCEN. Reputable exchanges like Coinbase and Kraken provide clear reporting, maintain segregated client funds, and undergo regular audits. These exchanges enforce KYC and IP-based geo-restrictions based on their operating jurisdictions.
Services offered by exchanges:
- Matching engines for exchanging assets off chain
- Derivatives (depending on your jurisdiction)
- Hot wallets for digital assets
Institutional Custody Risks
Qualified custodians are generally a safe option for storing digital assets due to strict regulations, but they come with their own trade offs. Heavy regulatory oversight introduces overhead, constraining liquidity and slowing asset movement. Organizations should be prepared for an extended onboarding process and higher operational fees if they use a qualified custodian for their digital assets.
According to the FTC and SEC, cryptocurrency exchanges outside the U.S. still operate in regulatory gray areas, often offering exotic products or potentially manipulating client funds. The 2022 collapse of FTX is a notable example where client assets were commingled with funds from Alameda Research, an affiliated trading firm. Ultimately, this led to billions of customer funds becoming frozen and unrecoverable. Their U.S. subsidiary, FTX US, was not immune, leaving many U.S. customers exposed due to insufficient regulatory oversight. Exchanges can operate with opaque incentives, internal trading desks, or market making operations that can amplify counterparty risk. Evaluating an exchange's compliance record and corporate structure can help mitigate risks associated with holding digital assets in exchange-managed wallets.
Self Custody
For some organizations, self custody strikes the right balance of security, liability and flexibility. Organizations frequently transacting with digital assets, or regularly moving funds between crypto and traditional finance, should consider self custody. Holding digital assets internally can help mitigate institutional risks, such as counterparty insolvency, regulatory actions, or operational disruptions. For example, a business that accepts crypto payments, with reserves too large for FDIC insurance but too small to justify costly credit default swaps, can combine self-custody with derivative instruments to manage financial risk effectively.
Best Practices
To securely implement self custody, organizations should adopt strong internal controls and policies, focusing on these key areas:
1. Use Multi-signature Wallets for Critical Funds
Multi-signature (Multi-Sig) wallets are fundamental for securing digital assets. These wallets require multiple private keys to authorize transactions, thereby eliminating single points of failure. A common setup might be a "3-of-5" multisig wallet, meaning three of five total keys are required to approve transactions. Multi-sig structures align with most organizational hierarchies and ensure transactions require multiple layers of authorization.
2. Securely Distribute Keys in Cold Storage
By default, organizations should store private keys offline in secure, geographically distributed "cold storage" solutions. Secure hardware devices or NFC-based devices can hold these keys safely. Implement role-based access controls and documented access procedures. An organization should retain control over several keys internally, while entrusting a portion of keys to external custodians or trusted partners under strictly defined policies.
3. Implement Policies and Procedures
An oversight committee should be created with strict separation of duties. Document key generation meticulously (video documentation is recommended). A Treasury Management System should run anti-money laundering (AML) and velocity checks before transactions receive final approval. All blockchain transactions must be internally documented and logged in a secure audit trail. Secret keys should be rotated whenever the stakeholder structure changes significantly, or at regular intervals.
4. Build a Backup and Recovery Strategy
Each private key associated with a multi-sig wallet can be lost or compromised, so robust backups are essential. Organizations should consider leveraging Shamir’s Secret Sharing algorithm, which divides a single key into multiple shares, requiring a predefined threshold of shares to reconstruct the key. Because recovery procedures involve coordinating multiple participants, organizations must regularly conduct tabletop drills to prepare stakeholders for potential disaster recovery scenarios.
5. Regularly Audit and Test Controls
Routine security audits performed by external experts are strongly recommended to ensure the integrity and robustness of custody systems. Organizations must remain vigilant against emerging threats, even though cold storage significantly reduces common vulnerabilities. Internal procedures, key integrity, and backup availability should be tested and verified regularly, ensuring all systems remain secure and operational in a state of emergency.
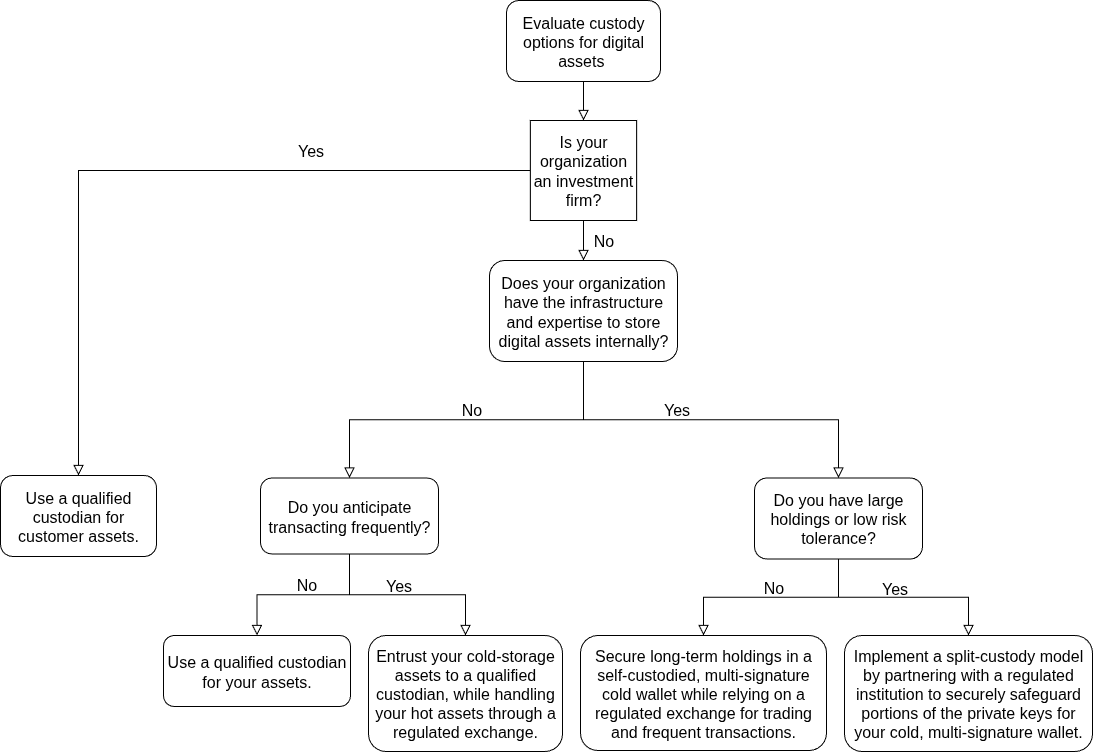
Decision Tree
To assist your organization in selecting the most appropriate custody approach based on operational needs and risk tolerance, refer to the following decision tree: